Tal Simhayev

About Me
Hey there! I’m Tal Simhayev 👋
I like to participate in CTF events with my team, mainly focused in categories like binary exploitation and reverse engineering (Scored 18th place in pingCTF-2023 - See below).
In addition, I worked together with my team to bypass modern defenses like ASLR, DEP, and PIE.
Projects
Exploited PrintDemon (CVE-2020-1048)
-
Privilege escalation to SYSTEM via a Windows Print Spooler logic vulnerability
-
Overwrites PrintConfig.dll through a crafted print-to-file job, then starts an XPS print to load the DLL and spawn a SYSTEM shell.
Exploiting PrintDemon for Privilege Escalation (CVE-2020-1048)
🐄 Exploited Dirty COW (CVE-2016-5195)
-
Privilege escalation vulnerability in the Linux Kernel 🐧
-
Tools Used: C, Linux Kernel
-
Successfully crafted an exploit to a race-condition in the kernel to achieve root access.
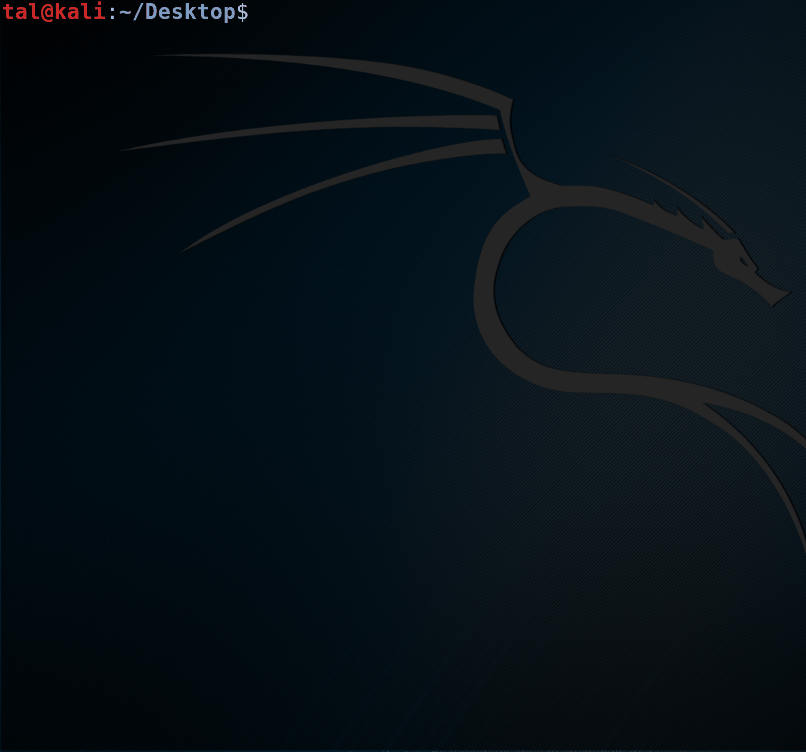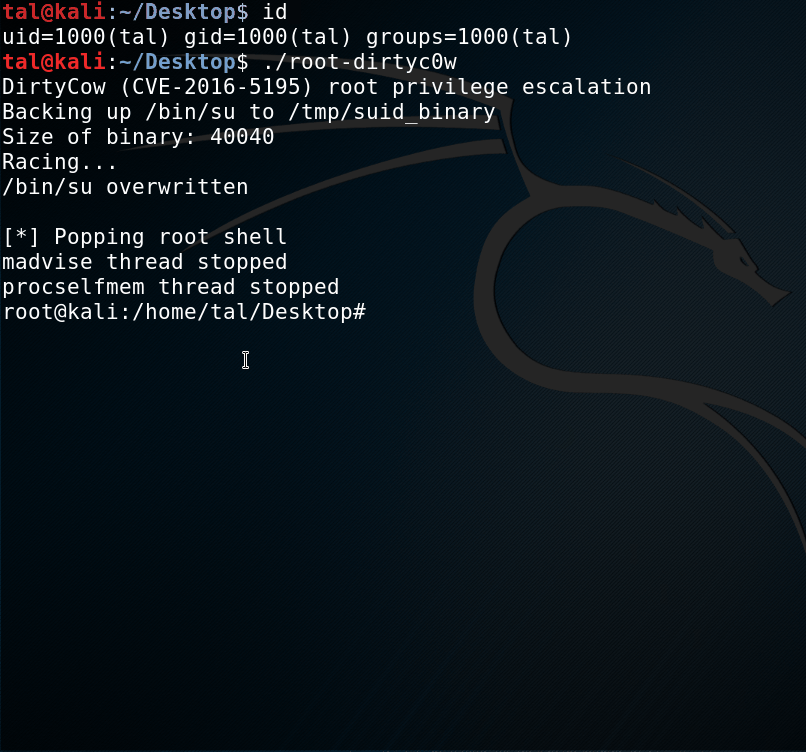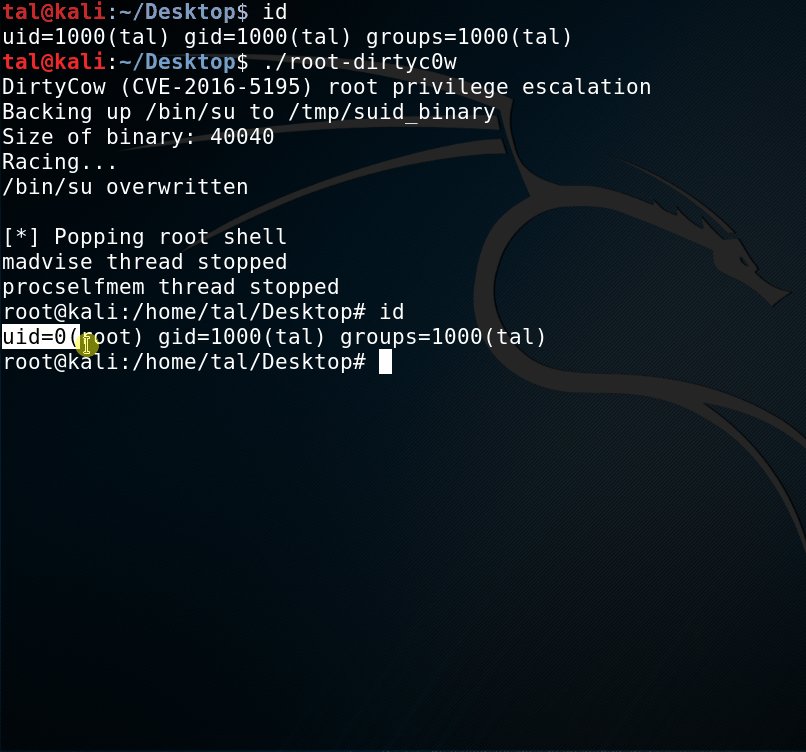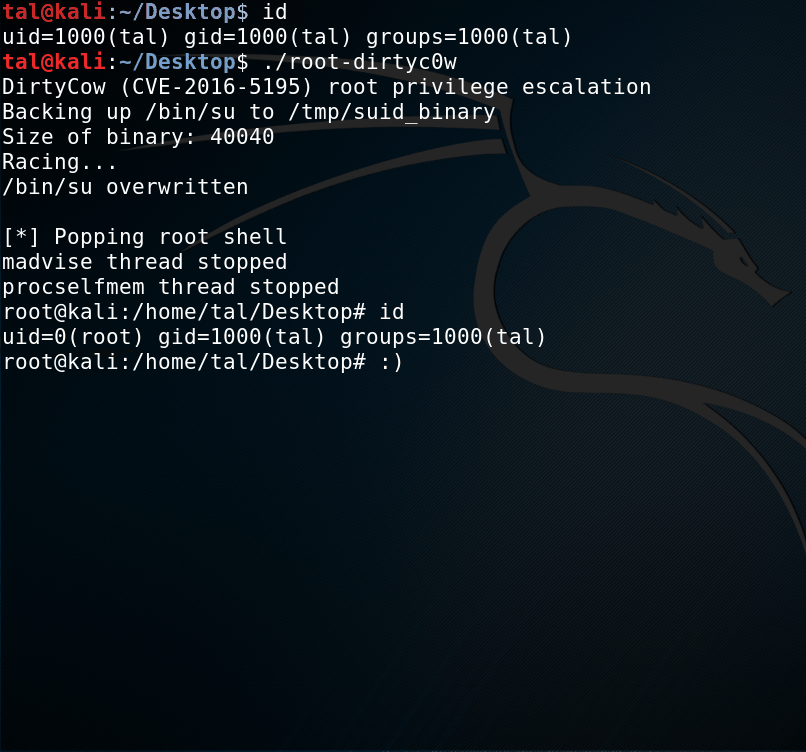
Privilege Escalation exploit: Exploiting Dirty COW for Root Access (CVE-2016-5195)
🐴 CloakRAT
- Remote Access Trojan (RAT) written in C/C++.
- Evades AV detection from Windows Defender.
- Injects itself to processes using DLL Injection.
- Implements anti-debugging techniques, junk code obfuscation, PEB Walk and C2 Communication.
KeyLogger (C/C++)
- Used Windows Hooking API to log keystrokes 📃
- Implemented persistence through Windows Registry modifications 🗝️
Implemented Linux shell
- Custom-built shell in C.
- A deep dive into Linux Internals.
HashMap & LinkedList in C/C++
- Implemented core data structures like HashMap and LinkedList in C/C++ for efficiency and memory management (Used when I implemented a shell in Linux).
CTF Write-ups & Blogs
I regularly participate in CTF events with my team, C0d3-Bre4k3rs, focusing on binary exploitation and reverse engineering.
Below are some of my write-ups:
Flare-On 2024 Write-ups
-
Documented solutions for 4 challenges from the Flare-On 2024 CTF.
-
Focused on reverse engineering and binary analysis techniques.
pingCTF 2023 dangle-me pwn challenge write-up
-
Developed a working exploit for a memory corruption vulnerability
-
Focused on stack-based buffer overflows and Return Oriented Programming (ROP) techniques
-
Bypassed PIE Mitigation by leaking addresses from process memory
-
Check out the exploit on Github.

pingCTF 2023 dangle-me exploit
ROP Emporium write4 - Blog
-
Crafted an arbitrary write exploit (write-what-where condition) to inject data to memory and bypass DEP protection
-
Published on Medium, it showcases how to chain ROP gadgets effectively.
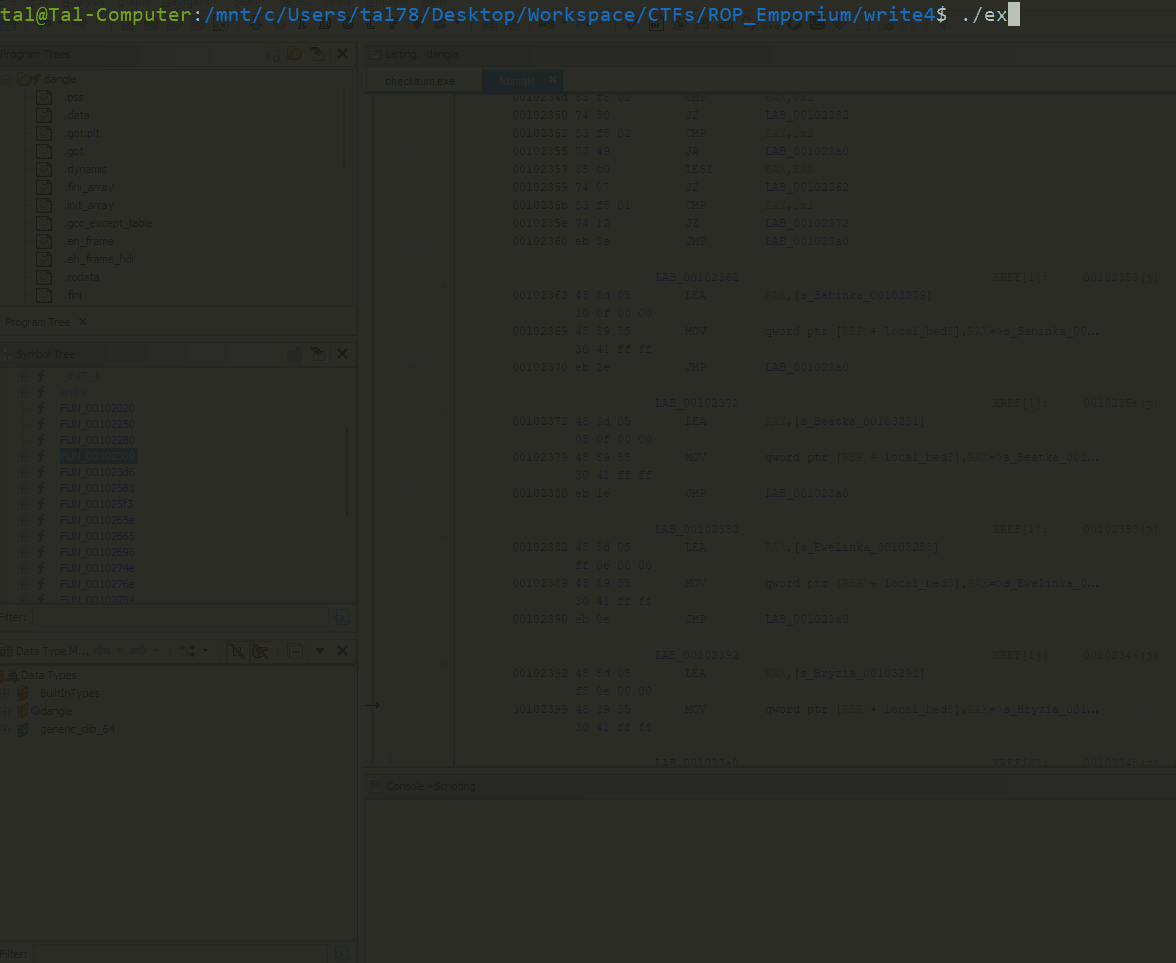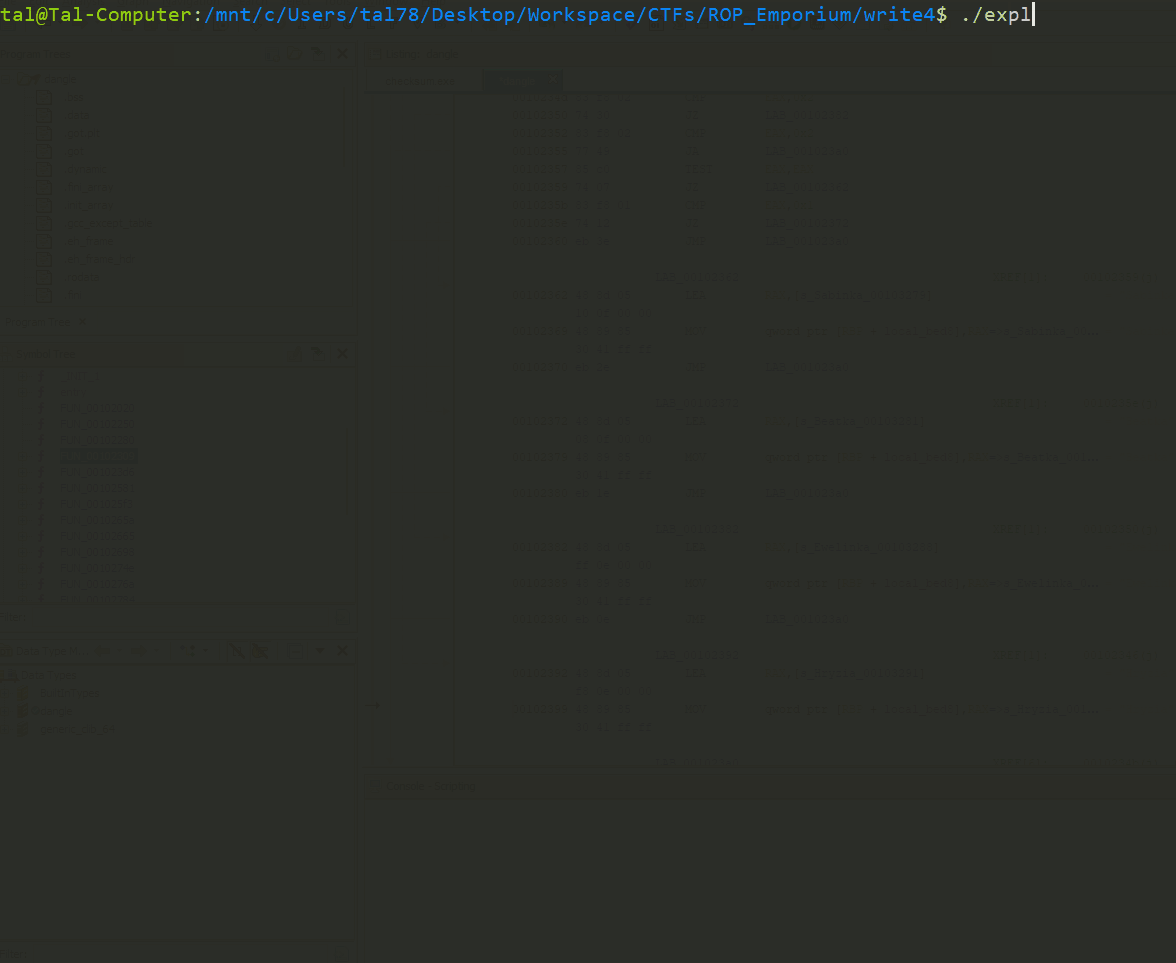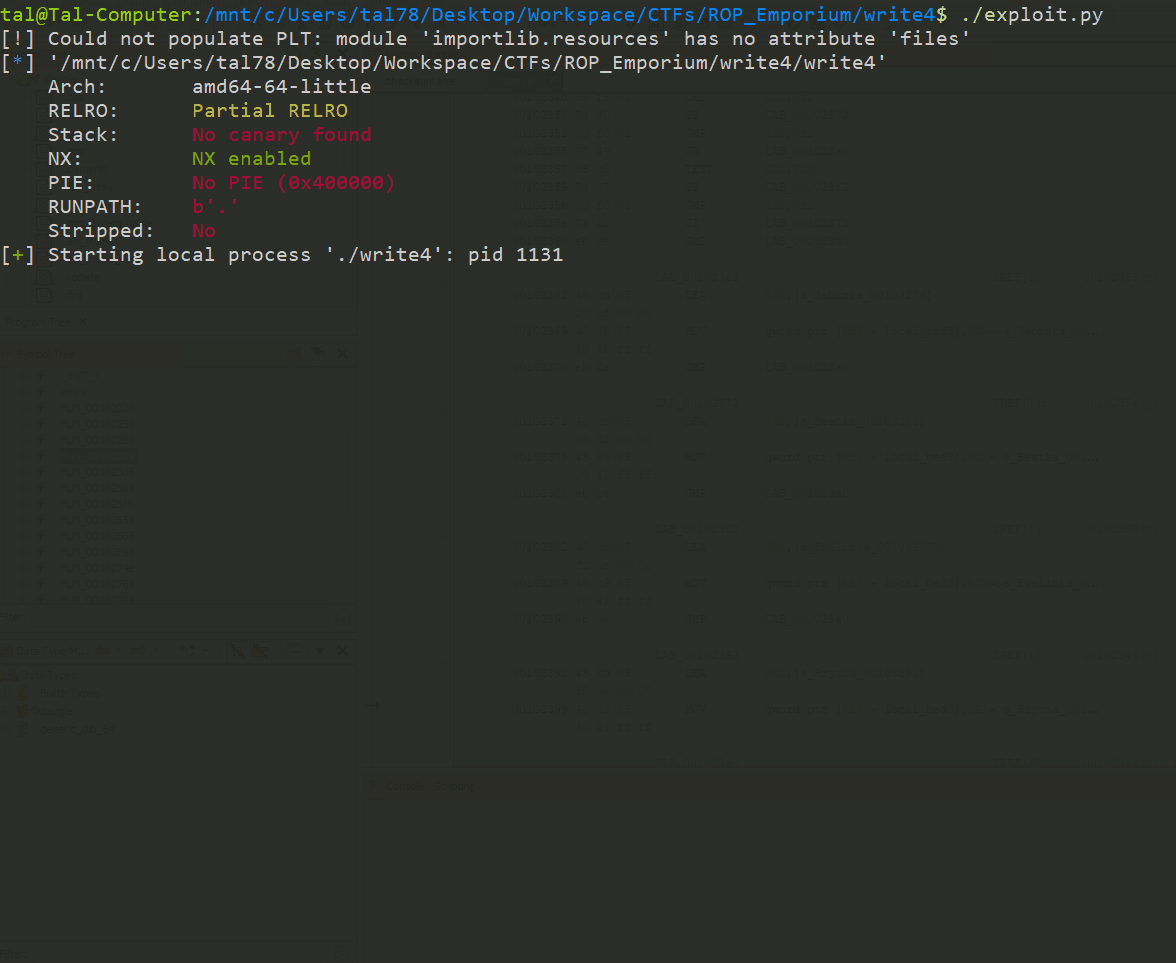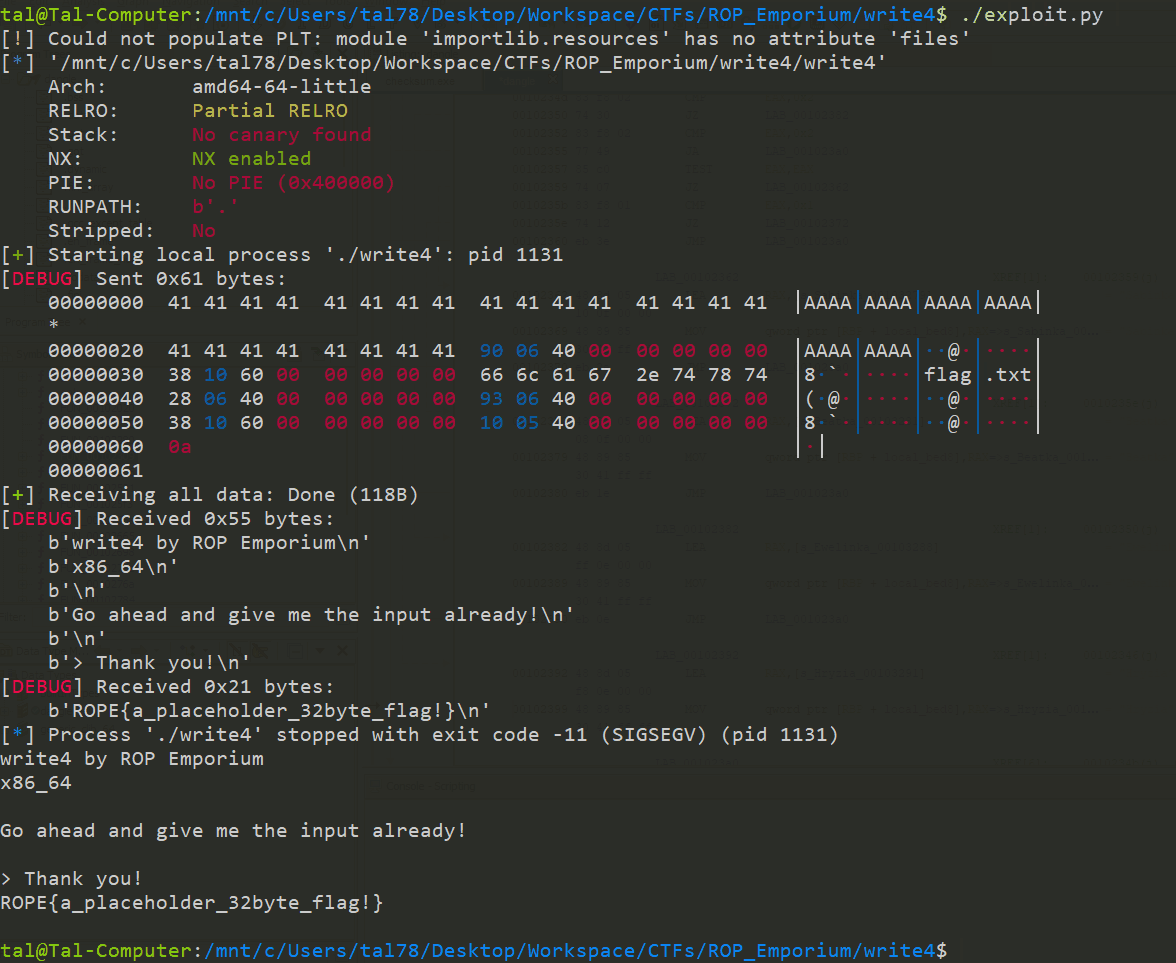
ROP Emporium write4 exploit

